The Linux-targeted malware is now an open source code ripe for further abuse

In response to last week’s massive DDoS attack on Dyn – which used the same network of hijacked IoT devices infected with the Mirai malware as earlier attacks this year – one company whose webcams were affected will be initiating a massive recall, perhaps the first of its kind.
According to the company, Hangzhou Xiongmai Technology Co., only devices produced before April 2015 were affected and it primarily blamed end users for not changing default settings. Though the company initially told Reuters that only 10,000 cameras were affected and subject to recall, it will in fact be recalling over four million units in total. This includes, according to Threatpost, “one million cloud network cameras, one million panoramic network cameras and 1.3 million network cameras.”
Before last week’s DDoS attack, security researchers from Flashpoint found over half a million vulnerable devices online, worldwide. “There is nothing stopping the average software developer from creating their own bot code,” The Register tweeted: “The problem is not Mirai – it’s crap IoT security”. Although the devices do not hack targets, their mass spamming to effect a DDoS is sufficient to shut down even large websites such as Reddit and Twitter.
Also Read: Japan comes looking for Israeli cyber security startups
DVRs and CCTVs alongside webcams are among the most vulnerable IoT systems. Firmware updates to DVRs, for instance, have not been uniform across the industry to rectify this problem. Several years have passed since the problem was widely flagged, and DVRs are still in general very easy to crack. CCTVs have been used to effect major DDoS actions since 2014, initially through the use of BASHLITE malware. Just about any IoT device could be shanghaied, like a baby monitor or “smart home” tool, and absent bad PR or lawsuits, these companies have little incentive to develop more security solutions.
These devices remain vulnerable, according to Brian Krebs, because, “while users could change the default credentials in the devices’ Web-based administration panel, the password is hardcoded into the device firmware and the tools needed to disable it aren’t present.” The problem is further compounded by the fact that many Xiongmai components are used by other manufacturers, not just XM-branded products, such as Panasonic, SNC, and ZTE.
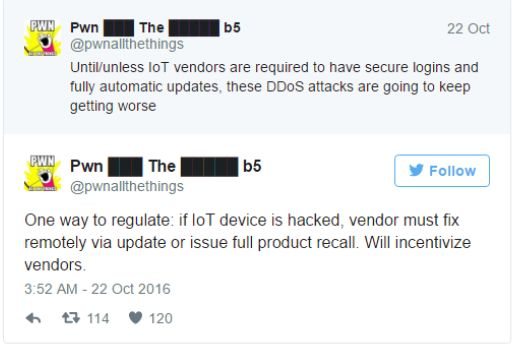
Since the Mirai botnet homes in on default admin settings, even a “strong” password is not going to defend against it. Moreover, if a compromised device is restarted and not reset fast enough, it will still be vulnerable to Mirai.
Also Read: HARMAN acquires Israeli cyber security startup TowerSec for US$75M
The biggest challenge will probably be breaking developers of the habit of using these default settings, according to a Facebook post from Crosswire founder Ron Reiter. Even if that could be accomplished by regulation or fines in one jurisdiction, to go about it globally is another matter entirely, though if people start suing companies like Xiongmai over the downtime costs associated with DDoS attacks launched via their hijacked products. Another issue, noted by Parker Higgins of the Electronic Frontier Foundation, is that anti-circumvention laws in the US do not exactly encourage research into the problem.
So while IoT security spending will continue to rise in the wake of these attacks, the consultancy Gartner nonetheless, “predicts that by 2020, more than 25 per cent of identified attacks in enterprises will involve IoT, although IoT will account for less than 10 per cent of IT security budgets.”
—
The article Mirai botnet infected so many Chinese-made webcams they have been recalled first appeared in Geektime.
Image Credit: 4ivers / 123RF Stock Photo
The post Mirai botnet infected so many Chinese-made webcams they have been recalled appeared first on e27.